Every system update is tremendous work of developers who release patches to fix cyber vulnerabilities. However, no company has enough resources to fix everything immediately. What are the most popular vulnerabilities used by hackers
Why you can’t fix everything at once
In 2020, the world recorded about 50 new vulnerabilities every day, according to Cyware study. NTT Application Security has calculated that the average time to resolve serious vulnerabilities is increased from 194 days at the beginning of 2021 to 246 days in June. And the total number of identified vulnerabilities this year was 18,266, according to the portal CVE Details.
Even large technology corporations that create products for millions of users are unable to cope with this load. Threat intelligence exists to prevent or mitigate potential attacks.
A survey of information security specialists from Positive technologies showed that the most time-consuming process for small businesses is the analysis of scan results. It takes up 50% of all working time. And for medium and large businesses, the most time-consuming process is to agree on the installation of patches – 55% and 56% respectively.
Threat investigation allows you to optimize these tasks. Companies can eliminate vulnerabilities in software and applications in advance and ensure the smooth operation of the system.
How to analyze vulnerabilities
Popular risk management services are Qintel Patch Management Intelligence, Tenable.io, Rapid7 Threat Command.
Each vulnerability is assigned a unique CVE-year-number identification number. All information about CVE is registered in the database of well-known information security vulnerabilities. MITRE supports updates to the CVE database.
What vulnerabilities are most often used by hackers
In Darknet, hackers share exploits – source code that exploits specific vulnerabilities that each cybercriminal can adapt to his or her own needs. This contributes to the spread of vulnerabilities and the growth of cybercrime. CyberSEALs experts have identified a list of the most relevant CVEs that have been tracked and used by hackers over the last five years:
CVE-2017-11882
This is a vulnerability in Microsoft Office 2007, 2010, 2013, and 2016. It allows the attacker to run arbitrary code on the victim’s device and thus remotely execute commands. The hacker gains control of the device and the data it contains. The vulnerability threatens any device on which these programs are installed. This vulnerability is most popular because of its versatility. It has existed in Microsoft products for 17 years and has repeatedly proven its effectiveness.
CVE-2017-5070 and CVE-2020-164
Vulnerabilities in Google Chrome for Linux, Windows, Mac, and Android allow an attacker to create an HTML page and execute arbitrary code on the victim’s device. In this way, the attacker gains access to all user data.
CVE-2017-0199
This vulnerability threatens Microsoft Office 2007, 2010, 2013, 2016, Windows Vista, Windows Server 2008, Windows 7, Windows 8.1. An attacker creates a malicious RTF file that opens in the listed Microsoft programs and executes code and hacks into the victim’s device. This allows the hacker to download the ultimate virus to the device and use it to infect not only the victim’s computer but also other devices in the network.
CVE-2019-19781
Vulnerability in Citrix Systems, which specializes in server, software, and computer virtualization, software, and cloud computing technology. It allows executing arbitrary code in the Citrix Application Delivery Controller and Citrix Gateway, accessing the physical device, and performing any action with it.
2021 trends
Over the past year, hackers have been actively exploiting vulnerabilities in Microsoft solutions: Office, Windows 7, Windows 10, Edge, Internet Explorer, Windows Server 2008. And the most vulnerable systems in 2021 were Google Chrome, Microsoft Office, Microsoft Exchange Server, Microsoft Server Message Block, Windows 10, and Windows Server 2008.
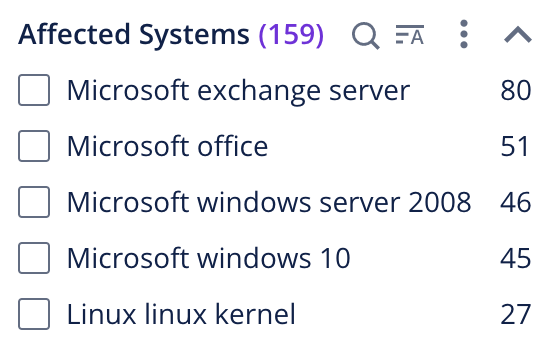
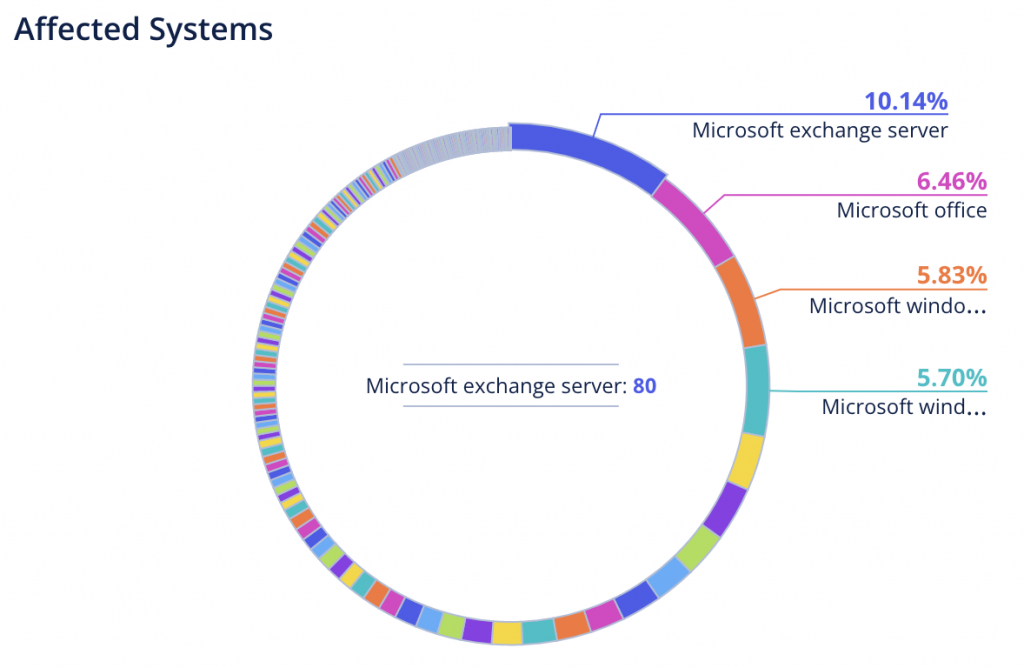
Web application attacks are also very popular among cybercriminals. The most vulnerable web solution systems in 2021 were WordPress Plugin JS Jobs Manager, FlatCore CMS 2.0.7, Confluence Server 7.12.4, XAMPP 7.4.3. Each of the vulnerabilities allows an attacker to gain access to the attacked devices and included data.
All these programs and applications are very popular. It would be challenging for businesses to stop using them. That is why we collected the general guidelines that must be followed to protect your organization:
Source: Forbes Ukraine