Cybercrimes are becoming more sophisticated by the day, and victims’ financial and reputational losses are ramping up as a result. According to Netscout 2020 estimates, more than 26,000 cyberattacks occur every day, or 18 per minute, around the world. CyberSEALs has prepared a series of articles titled “Digital Footprint” for you in which we describe real-life cases of our clients and explain how to prevent cybercriminals from causing harm to your organization.

Despite the widespread belief that cyber criminals must possess exceptional technical knowledge and skills, it has been discovered that only a small number of attackers are truly qualified IT experts. The vast majority of online attackers are ordinary citizens looking for ways to make money by exploiting information security flaws in businesses, governmental institutions, and even critical infrastructure institutions. Cyber attacks are one of the most common types of illegal activity on the Internet. According to IBM and the Ponemon Institute research “The Cost of Data Loss”, which surveyed over 3,000 IT and security professionals from 17 countries, the average financial cost of data loss globally in 2020 is $3.86 million. Today, we will tell you about a cyberattack on one of Ukraine’s banks, which was investigated by CyberSEALs specialists.
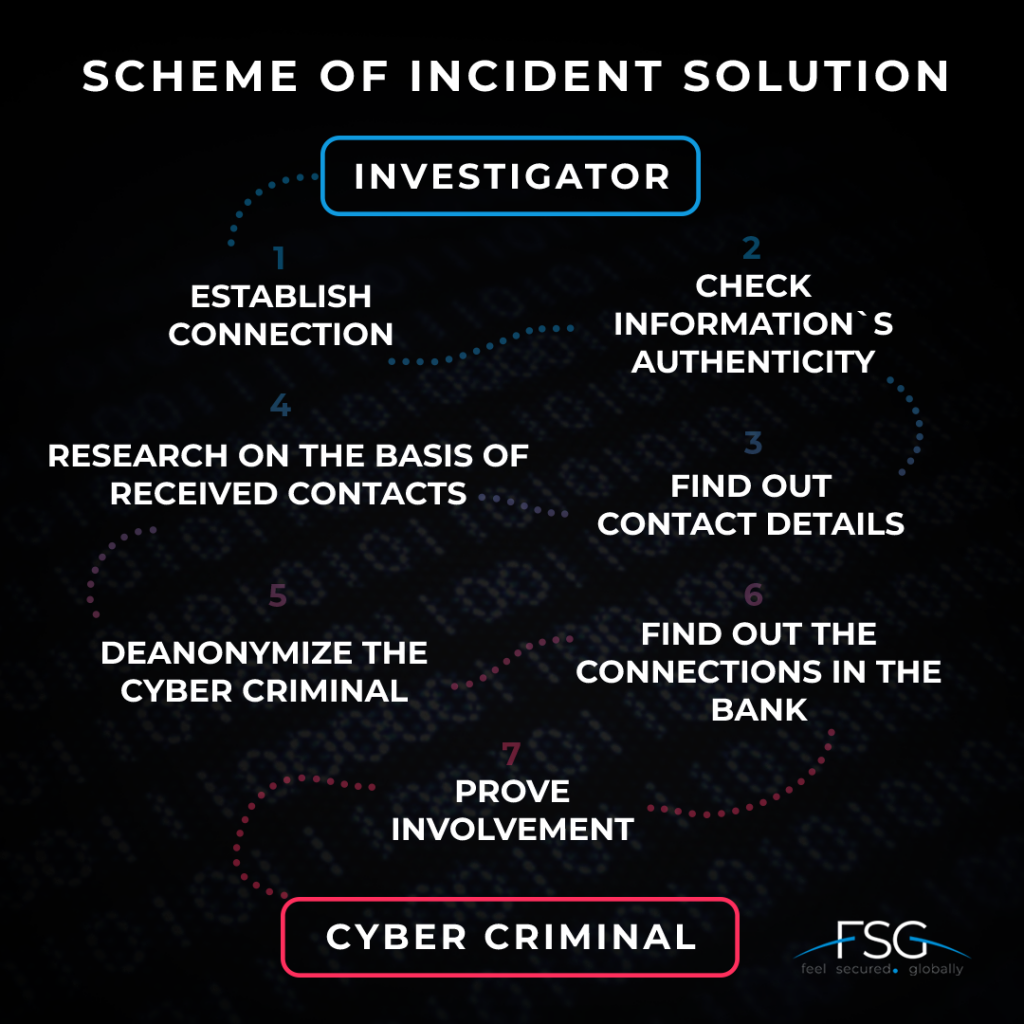
CyberSEALs experts discovered an offer to sell confidential information of clients of one of Ukraine’s banks while monitoring hacker forums on the Darkweb. The R&F (research and forensic) team started looking for the attacker.

“The beginning of the investigation was the search for offers on the sale of information of Ukrainian banks’ clients in Darkweb. Since information is a perishable product, cybercriminals usually place advertisements for the sale of data within 1-2 days from the date of theft. Of course, if their goal is not to blackmail the companies from which they stole the data,”
notes Eugene Volchok, an investigative expert at CyberSEALs
According to the monitoring results, the person who listed the item for sale completed application forms for banking services, photographs of bank clients, passports, and bank cards.
“Hacker forums are not always easy to find. Their addresses are passed down through word of mouth and are constantly changing. To enter the necessary forum, you must have both technical skills and information from the cybercrimes` world,” Eugene adds.
In DarkWeb it is common to deceive buyers of prohibited products and services because sellers leave minimum information about themselves. Payment is made in cryptocurrency or through anonymous payment services, making it nearly impossible to identify the final recipient of funds. To verify the validity of the data offered for sale, it was necessary to make contact with the seller and obtain a portion of the data from him for further verification. After confirming the accuracy of the data, CyberSEALs experts began their investigation.
“A guarantor is a job that exists on the Darknet. It is a person who acts as a mediator for the buyer and seller. Their services are used to reduce the risk of fraud during the transaction, and because the guarantor typically receives the requested sum from the buyer in cryptocurrency and sends it to the seller in any convenient manner,”
Eugene explains.
The first contact with the attacker was made through a guarantor. When the cyber criminal was convinced that the investigator could be trusted, he agreed to communicate directly and provided a personal phone number. This was a critical step in de-anonymizing the offender. The provided number was only used for payment transactions by the cybercriminal. Furthermore, the phone number helped in determining the details of the attacker’s e-wallet. By using this information, the expert gained access to a personal account in one of the Ukrainian banks, from which the cybercriminal withdrew funds.
The R&F department used data from payment services to establish his identity using OSINT and CSINT tools. OSINT and CSINT are technologies for retrieving data from different sources of information. CyberSEALs has developed its own OSINT and CSINT tools, which, using unique algorithms, allow us to conduct highly efficient and fast information research to investigate cyber incidents.
“It is critical to not only identify a person but also to demonstrate his or her attitude toward cybercrime. Hacked accounts and gadgets are frequently used as cover by experienced criminals. As a result, the most responsible aspect of the work is determining the suspect’s involvement,”
mentions the expert.
Investigators examined the documents that had previously been purchased from the attacker. Some of them bore the name of a bank employee who interacted with customers. Based on the document analyses, it was also possible to determine the time they have created and the possible bank branch address from which the data was stolen.
The R&F team then looked through the employee’s social media pages to see if she had any connections to the person under investigation. Experts made two assumptions based on this discovery. The first is that the suspect could be a bank employee. Second, the employee could be a part of a criminal conspiracy.
To confirm or refute the hypotheses, the CyberSEALs investigator checked the defendant’s information in Ukraine’s Unified State Register of Court Decisions and discovered an administrative penalty imposed on him previously. The document included the offender’s current place of employment, among other things. This helped to establish that the suspect is a bank employee who illegally sells confidential information about customers on DarkWeb. The involvement of a girl who also works in a bank has not been proved.
“We spent about three months on this investigation. From time to time, the criminal was disappearing and deleting the correspondence. So we had to reconnect several times. This is a common practice, especially when the hacker is not an experienced one and does not know how to ensure his privacy. The organization`s big data provided a great contribution to this case. It contains the world’s largest amount of data on cybercriminals, illegal forums, etc.”, sums up Eugene.
CyberSEALs emphasizes that the most effective protection against cyber attacks and data theft is to prevent them. Companies must take into account the risks of rapid digitalization. The case of the bank describes one of the most common scenarios when cybercriminals join a company to carry out illegal activities for their enrichment.

Our company offers an FS IRT service, which provides an effective solution for investigating cyber incidents. The service includes consulting with security experts, investigation of specific information security incidents, comprehensive forensic investigation of digital evidence of cybercrime, providing client and personnel reports from various sources, creating a monthly newsletter with individual recommendations, penetration testing, web scanning of applications and resources. CyberSEALs creates the most effective security solutions for businesses. We work to eliminate the risks of cyber incidents for our customers.